Today's embedded systems often handle sensitive information such as application code (IP) and data, so security is a major concern in their design. In order to establish a reasonable basis for judging whether the proposed security system is sufficient to defend against enemies or defenses, it is necessary to identify perceived security threats. This means we need to figure out what the opponents have, what capabilities they have, and what are their goals? What do we want to protect, who are we to guard against or what threats? There is no one-size-fits-all solution in the world, and there is no one-hundred security system. However, the security system does not have to be a flawless solution, nor does it need to be completely unbreakable to lose its application value. The security system can be as secure as possible, that is, it can withstand possible enemy attacks within the expected effective time of the data it protects.
If there is no application environment, security is meaningless.
Embedded system designers often misunderstand security and believe that security measures such as specific encryption algorithms and security protocols are just additional features of the system. Security is a process, not a product or an ultimate state that will remain the same forever. Moreover, security measures cannot be simply added to a product under the assumption that the product will remain safe forever. One of the toughest challenges facing designers today is to define the security requirements and goals of embedded systems. There are many ways to solve this problem. The methods discussed in this paper involve threat modeling and risk assessment. The goal is to help designers define security policies and then design countermeasures to implement security policies.
Safety design – detecting threats during the initial stages of design
When designing a security solution, the first thing you must do is define a threat model and then create a security policy. Once the assessment is complete, you can safely choose specific technologies to implement security countermeasures. The threat determines the response strategy and the strategy determines the design. See Figure 1
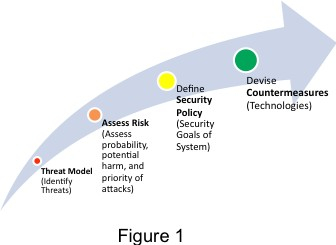
Figure 1 Designing a security solution requires (1) defining a threat model and (2) creating a security policy.
Many designers make the same mistake when designing a security system without first identifying and understanding the real threats they may encounter, and the significant risks these threats pose to their end products. Instead, they dogmatically put together various security technologies and hope to achieve high security. This is costly, no system can protect against all security threats, and it makes no sense to include in the design the risks of not having the necessary technology and defenses without real threats.
Threat modeling - value means risk
For resource-constrained devices, embedded systems must strike a balance between parameters such as storage capacity, power consumption, processing power, time to market, and cost. Despite the challenges of under-resources, it is possible to develop systems that make products work effectively in an open environment by carefully considering the threat model and designing the system to work within the available computing power constraints of the model.
It is useful for system designers to consider the principles of "threat modeling." Threat modeling is based on the assumption that each system has inherent value that is worth protecting. However, because these systems are valuable, they are also open to internal or external threats that can and often cause damage to end products. Security breaches after design are often uncorrectable and jeopardize the funding and development resources involved, so the need for security assessments needs to be enhanced during the initial stages of the design cycle and monitored and re-edited throughout the design cycle.
Essentially, we can define the threat model as: “Identify a set of possible attacks to consider a thorough risk assessment strategy.†With the threat model, we can assess the probability, potential hazard, and priority of the attack.
Threat modeling is difficult, but it is necessary. Threat modeling needs to consider how the system is attacked. If the modeling is successful, it can solve potential system security failures, such as how to fail, and what happens when the failure occurs. Often under market and cost pressures, this assessment is done in a special way, by brainstorming all possible attacks on the system (of course, potential hackers may be one step ahead of you). For this process, a more systematic and repeatable approach is to use the attack tree. This concept was first proposed by Bruce Schneier [1, 2]. The attack tree provides a way to systematically classify different ways of attacking the system. Roughly speaking, the system is described by a tree structure, and the nodes in the tree structure model represent attacks. The root node of the tree is the total target of the attacker, and the different path to reach the target is the leaf node, as shown in Figure 2.
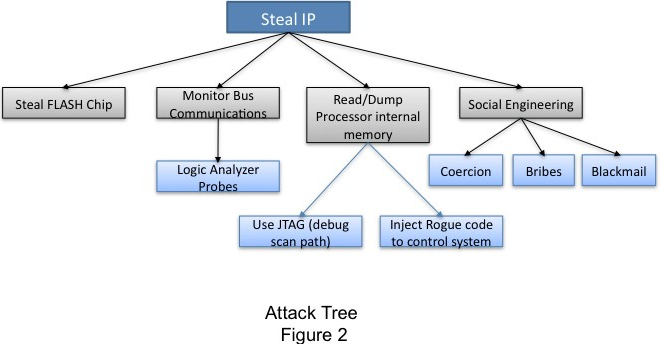
Figure 2. Attack tree representing any embedded system that must protect intellectual property (IP), including mobile phones, VoIP, video surveillance systems, etc.
When threat modeling is done correctly, the real threat is determined. However, if you mistake the threats that may exist, the cost will be high. One example of a designer's mistake in threatening is the DVD's protection. Although the DVD disc is encrypted and the key is placed in the player, as long as the player contains anti-tamper hardware, this protection method is no problem. However, when a software player is introduced, the key is exposed, the key can be recovered by reverse engineering, and any DVD content can be copied and distributed by anyone.
In this case, it is a flawed threat model. Although there are security measures, this does not really solve the problem.
Risk assessment
It's not enough to just list a bunch of threats. Because the risks of different threats are different, you need to know the risks of each type of threat. The next step in threat modeling is risk assessment, which is a vital part of any security system design. Some of the basic questions of risk assessment, namely “what to protectâ€, “why to protect†and “who is the object of preventionâ€, should be clarified at the beginning of the design cycle. Taking the measures shown in Table 1 as early as possible will help you choose effective and secure prevention technologies and defense strategies.
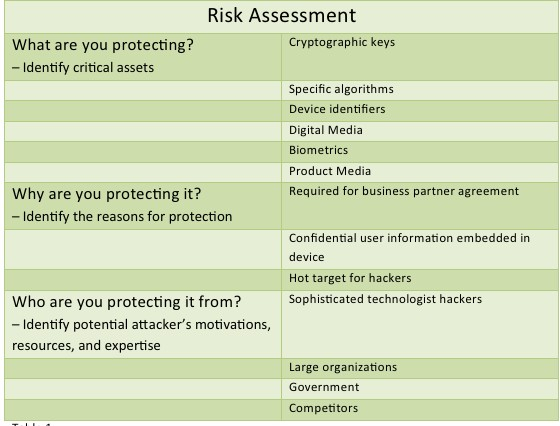
Table 1. Risk assessment
security strategy
Once you identify the threat and weigh the risks, it's time to set up a security policy. Security strategy is the strategy behind the solution, and technology is just a tactical tool. The security policy describes "why" rather than "how to".
For example, one of the security policy goals of FPGA-based design may be "keep the confidentiality of the configuration bitstream," which is a system goal. The "how to" or countermeasure implementation may be to encrypt the configuration bitstream in a manner that uses symmetric key encryption such as AES to achieve this goal.
The overall design process is summarized as follows:
Understand the real threats of the system and assess the risks of these threats.
Assess which threats are the most dangerous and most likely to occur.
• Describe and document the security policies required to systematically defend against these threats. This will be a series of statements, such as: "Only trusted code allows access to restricted memory", or "Password key must be kept secret."
• Design and implement preventive measures that enhance the system's security strategy. In theory, these precautions are a hybrid mechanism for protection, detection and response.
Precautions
Once a potential attack has been identified and a security goal has been defined, consider implementing a prevention technique to mitigate the risk. An effective set of security precautions consists of three distinct parts: protection, detection, and response. These countermeasures must work reasonably together based on known threats to the system. If the protection mechanism is compromised, it must rely on detection and response mechanisms to defend against attacks. If the response mechanism does not exist or is invalid, then there is no point in having a detection mechanism.
In embedded systems, protection, detection, and response techniques can take many forms (see Table 2). These technologies work together to block potential attacks or provide useful court review information after an attack.
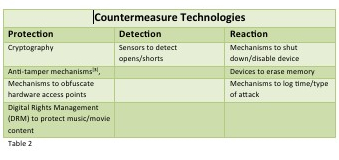
Table 2. Prevention techniques
Conclusion
Security design is a dynamic, system-specific process that is often complex. For each of the security topics discussed in this article, there is a wealth of research and technical expertise for designers to research and learn. When designing begins, the most important thing is to start a security needs assessment as early as possible, define system security goals, and regularly determine whether the initial threat has changed or expanded based on system usage and market changes.
When do you know that the system is safe enough? Robbie Sinclair, responsible for security at Country Energy in New South Wales, Australia, once said: “Safety measures will always be excessive before you feel safe.†When you start a safety assessment, give you “how much safety†The answer to this question is safe.
Philip Giordano is a Senior Applications Engineer at Analog Devices. He joined Analog Devices in 1998 and is currently responsible for new product development for embedded processors with a focus on security features.
The Flexible LED strip lighting from Win3 safety is a perfect solution for a wide variety of industrial lightingand decoration applications including; cove lighting, under-ground lighting, mining/tunneling opearation, yard/lawn lighting and decorative lighting.
Our Ultra Bright flexible LED strip light is 36V DC voltage and IP 67 water proof level, with 120 Led/M, it illuminates at 6500K. PCB color, length, Led quantity all can be customized.
Extremely long life: up to 20,000 hours with very low time-luminosity decay
Stripe Led,Led Fita Light,Harmony Led Strip,Striped Schoolhouse Light
ZHEJIANG HUACAI OPTIC-TECHNOLOGY CO LTD , https://www.win3safety.com