Over the years, I have only seen a few intrusions on televisions. Now in this increasingly intelligent era, everything is smart and everything is connected. This poses hidden dangers to a seemingly safe and intelligent life. This time, the television set was infiltrated for the set-top box of Tianwei Video. Don't be surprised, it's the TV.
With regard to the introduction of Tianwei Video, almost half of the TV terminals in Shenzhen are using Tianwei Video, and the huge amount of users will have serious consequences in the event of a problem.
First of all, this infiltration is also my whim, see the TV has an ip option, insert the network cable, and then after opening the set-top box will be able to get a series of information such as IP gateway.
Peeking inside the net
The IP is 10.97.143, the gateway is 10.97.128.1, the DHCP server is 192.168.222.105, and the DNS is 172.18.50.11 and 172.16.129.12.
This is a super large LAN. I thought that I could connect to an external network. It was actually a query page made by Tianwei himself. The server of the query page was connected to the external network. You could not connect the external network with the IP of 10.97.143.254. , tested on my computer proved this.
I chose to start exploring from the IP segment of this machine. I will fill 10.97.143 in the IISPUT to scan port 80,8080,23,22.
Did you see it? Both port 80, port 23, I immediately opened a page to view:
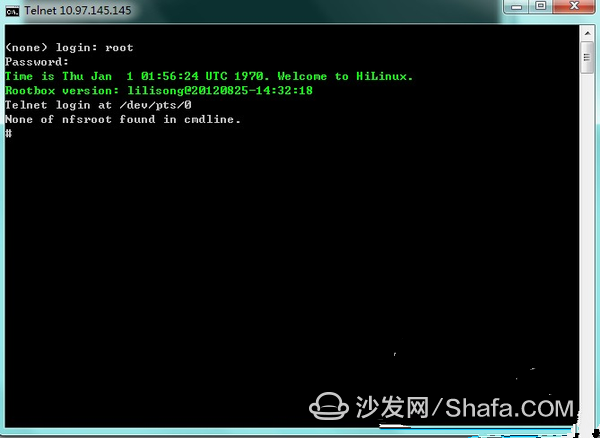
Test the connection with telnet:
Ok, you can connect, root empty password.
Landed successfully:
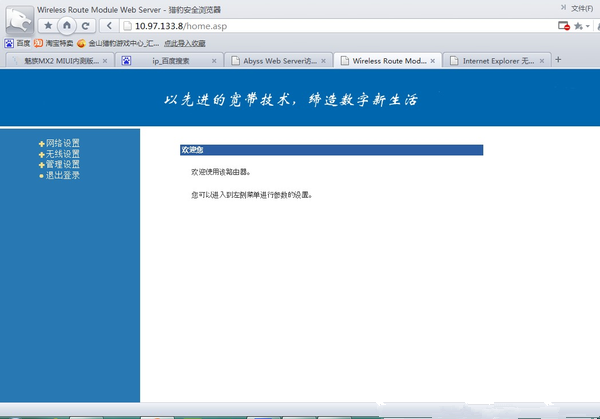
Through web access it is known as a router. After reading all the documents under the terminal, find something that penetrates further.
One hit kill
After I suddenly discovered this, see:
Seeing that, action, I thought, there must be a Struts command execution flaw, so I threw it into the use tool.
At the same time, I found a way to enter the routing, in fact, Tianwei's verification is very pitiful, just for home.asp this page, any other page directory is virtually empty so we can find where to change the password, directly modify the admin password.
This page is to change the password:
Landed in:
I had a preliminary scan, at least have more than 1,000 units, we can use this loophole to control thousands or even tens of thousands of wireless routers, the hazard can be imagined.
We went back to that Struts vulnerability, and I tested some of them, there is a Struts command execution vulnerability. Excited.
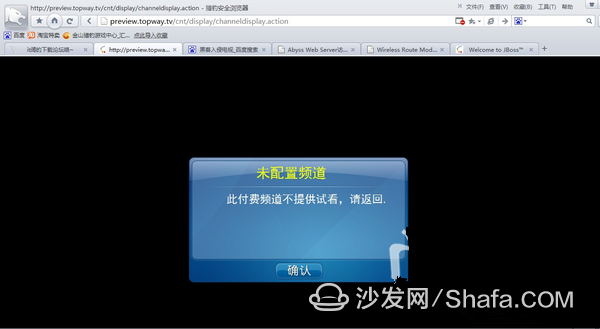
Do you know why I saw this picture excited? Because this is the screen displayed on the TV, some unpaid TV programs are this prompt, so that we can successfully modify the title and achieve the purpose of invading TV.
Continue further penetration to start with the DHCP server. The machine's DHCP server is 192.168.222.105, I tried to scan the 192.168.222.105 this section of the network ip, to see what can be used.
Wow, excited, so much ip, until I find this ip.
Run out of login user name and password:
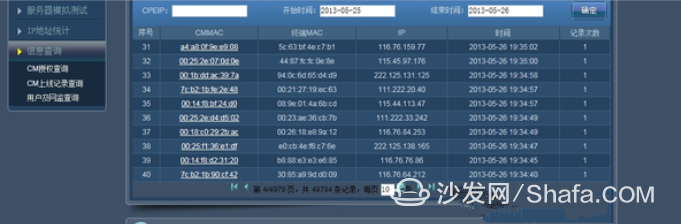
After coming in, I felt the bunker. Basically, all of Tianwei's ips I could query. Now we can query the on-line record of any set-top box.
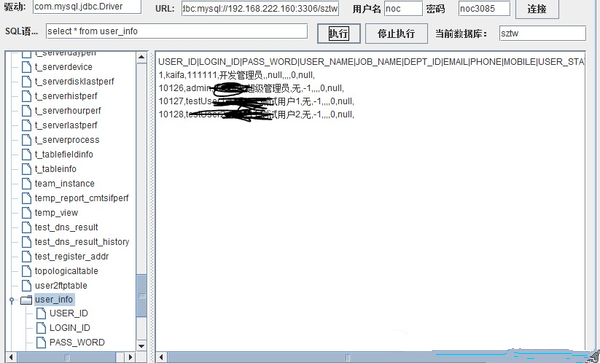
For further infiltration, I added an administrator account and logged in after 3389. After I logged in with the administrator user and opened Navicat for Mysql, many database leaks occurred.
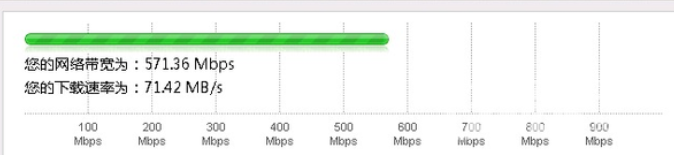
Predictable hazards. Look at this download speed.
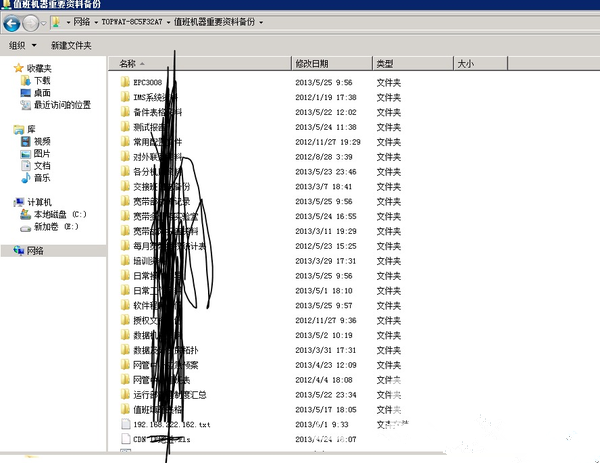
All internal data.
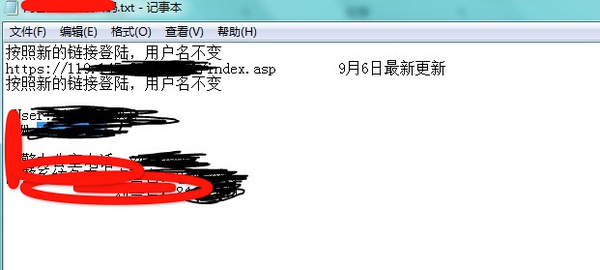
Take a look at these, if this information leaks disastrously. All are IMS devices. Are able to login.
Take a look at these, if this information leaks disastrously.
At this point, our infiltration has basically been completed. Although we can further in-depth, but because of the amount of information is too large, not much to say, be a small APT.
A siren is a loud noise-making device. Civil defense sirens are mounted in fixed locations and used to warn of natural disasters or attacks. Sirens are used on emergency service vehicles such as ambulances, police cars, and fire trucks. There are two general types: pneumatic and electronic.
Many fire sirens (used for calling the volunteer fire fighters) serve double duty as tornado or civil defense sirens, alerting an entire community of impending danger. Most fire
sirens are either mounted on the roof of a fire station or on a pole
next to the fire station. Fire sirens can also be mounted on or near
government buildings, on tall structures such as water towers,
as well as in systems where several sirens are distributed around a
town for better sound coverage. Most fire sirens are single tone and
mechanically driven by electric motors with a rotor attached to the
shaft. Some newer sirens are electronically driven speakers.
Fire sirens are often called "fire whistles", "fire alarms", or
"fire horns". Although there is no standard signaling of fire sirens,
some utilize codes to inform firefighters of the location of the fire.
Civil defense sirens also used as fire sirens often can produce an
alternating "hi-lo" signal (similar to emergency vehicles in many
European countries) as the fire signal, or a slow wail (typically 3x) as
to not confuse the public with the standard civil defense signals of
alert (steady tone) and attack (fast wavering tone). Fire sirens are
often tested once a day at noon and are also called "noon sirens" or
"noon whistles".
The first emergency vehicles relied on a bell. Then in the 70s,
they switched to a duotone airhorn. Then in the 80s, that was overtaken
by an electronic wail.
Siren and Alarm
Piezo Alarm,Siren And Alarm,Piezo Buzzer Siren,Piezo Buzzer Alarm Siren
Jiangsu Huawha Electronices Co.,Ltd , https://www.hnbuzzer.com