
I am a mobile phone. At the beginning of this year, the owner just spent a month's salary to take me home. We have just experienced a honeymoon and are preparing to stay together forever. When suddenly I one day, I was taken away by strangers and embarked on a lost journey that made me terribly frightened. As for how I lost, and the distances I traveled, why did my little friends disappear erratically? Check out the black industry chain behind the stolen phone.
First of all, I will teach you how to comfort a person who has just lost his cell phone:

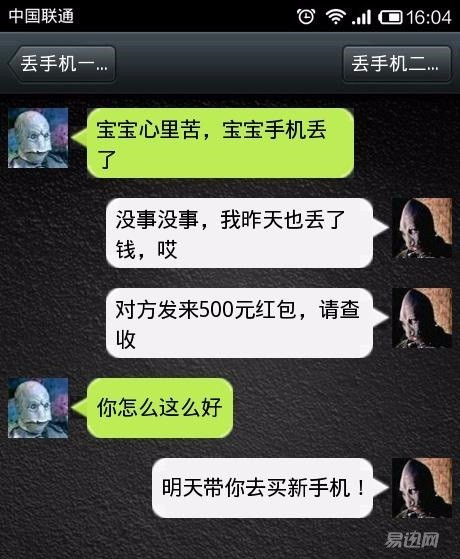
Thief stealing a mobile phone is actually driven by interest

Take an iPhone6s just listed. For example, the first-hand income of a thief ranged from 400-800. After that, there was probably more than 500 profit margins for each handed business. The income of whitewashed and refurbished merchants at the most source was higher. ! Speculation and crime are not surprising for such an unprofitable business. After a mobile phone (including iPhone and all other Android phones) is stolen, it will go through such a process
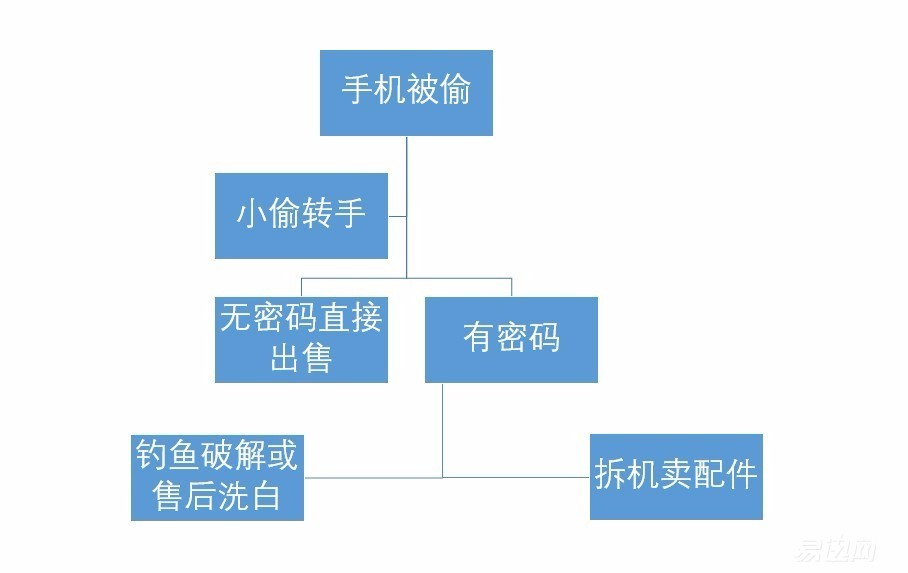
Today, we will mainly analyze and analyze the unknown black industrial chain after the mobile phone is stolen:
First, unencrypted mobile phones, thief directly sold, or sold to the acquisition of businesses
(This is where you really want to tell you, many years ago, when it was still a function and an era, business and public security were very strict about the management of second-hand mobile phones. They would check the procedures of second-hand mobile phones on a regular basis. If the procedures were incomplete, fines would be imposed on businesses. Detention, our family selling mobile phones, but this point of view is more profound, but now we can look at the physical stores and online sales of second-hand mobile phones are numerous, a lot of supervision weak.
Second, encrypted phone after the acquisition by the business
1. If you do a simple brushing process, there will be a part of the brand that is not safe enough to do it. In this step, the brand will fall and return to the first step to sell.
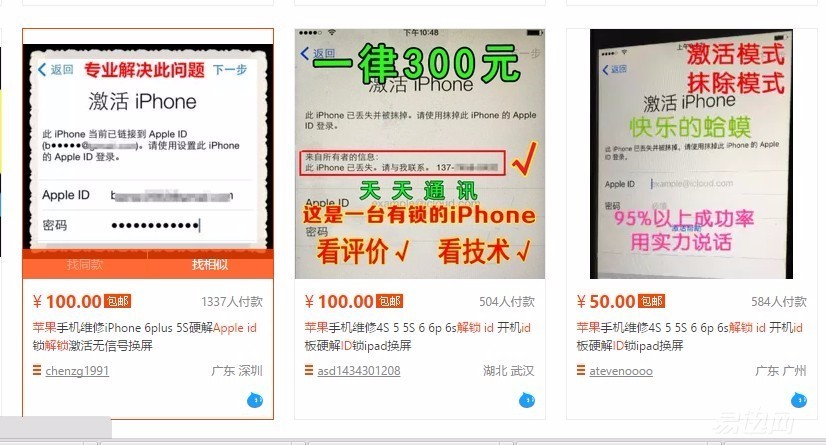
2. All parts of the country are sent back to Shenzhen in a unified manner. After all, as a bridgehead in China's mobile phone industry, Shenzhen is very powerful in both black and white. Locked mobile phones in Shenzhen will try to trick users through the phishing website to lock the ID information of the mobile phone, or colluded with some of the so-called official after-sales as mentioned in 3, and use the after-sales method to wash the mobile phone.
3. For second-hand merchants who have more methods and “internal relationsâ€, they will choose to return for repairs at the official after-sales in a certain place. The mobile phone that comes back after repairing can be used as a second-hand mobile phone, or it can be a simple refurbishment plus a box as a new mobile phone! In many places, it is now possible to do three-in-one, plastic seals, and a full set of accessories directly at the counter.

4. If this doesn't work, the mobile phone will eventually be disassembled and sold as an accessory. Now the original screen of the big screen smartphone is very valuable!
Apple has “officially authorized after-sales service centers†in various parts of the country. In fact, it is not operated by itself. Instead, it cooperates with local mobile phone distributors with better reputation or stronger capabilities. The workflow and specifications of these dealers in the face of consumers should be very strict. However, if it is too strict, many mobile phones that obviously should enjoy the Three Guarantees policy will not be served, which will greatly affect consumer acceptance of BNM. Therefore, the fact is that the standards of each authorization point are different. If there are one or two malicious "workers" and steal mobile phone channels, it is really not difficult to use this channel to use Apple's hand to wash white mobile phones! It can be imagined that the future of Apple will be more stringent for after-sales control.

Made in China, Meizu, for example, the Meizu cell phone I lost was obviously a password, and it couldn't be resolved by the flash format. But still after being stolen, they went back to the market and sold through certain channels. According to our brother who has been repairing mobile phones for more than a decade, the encryption of home-made Android is not very strong a year or two ago. High-tech people can indeed handle it. As long as it is technology, there must be loopholes. As for the situation in these two years, he only said that he could not tell me. They repair mobile phones, so much of the original accessories on the market came from everyone, in fact, everyone is crystal clear, and there is no better alternative method, the Internet xxxFIX Shenma, before it was also revealed this problem.
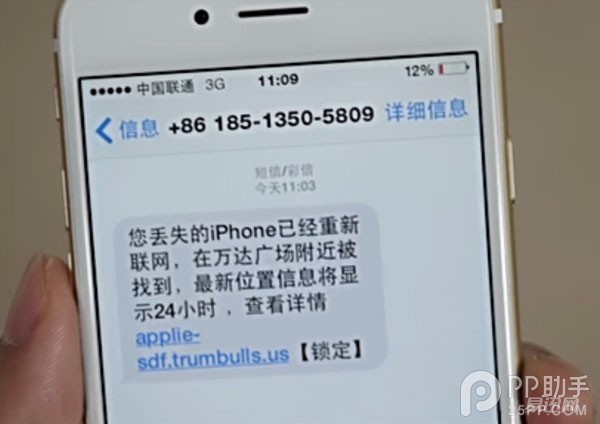
Although the method of stealing IDs by fishing may seem a bit low-level, it is the most convenient way for many people with less protective awareness. The phishing messages, emails, and web pages made by swindlers are very realistic, and they are easy to seduce people into.

In other cases, your mobile phone is clearly in your hands, but you are locked up by a liar and let you contact a QQ. This is the user data they exposed after cracking your NetEase or QQ email, or the theft of certain large forums, hitting your account. After you change your password, you must use this method to beat you. Don't compromise when you do this. They will never satisfy a first time money, but will cheat your so-called unlocking fees many times. This time directly contact the phone manufacturer, provide you with an account, or purchase vouchers will be resolved! If you are an Apple user, remember to turn on apple id verification twice!
For mobile phones, there is no encryption. Next time you must have a long eye! Increase the security on your phone!

The mainstream Android phones and iPhones on the market currently have the ability to remotely lock or search for a mobile phone with a login account. Even if it is brushed machine does not affect. In normal use, one or more of the password, gesture password, and fingerprint unlocking must be provided, not only for the sake of privacy of information, but also to make the best possible remedy for the loss of the mobile phone. There are a lot of embarrassing people on the Internet to get back their mobile phones. Everyone must learn and study. But the most important thing is not to be stolen! Because, even if you have 100 remedies, there will always be 101 responses for "smart thief". So not being stolen or key! !
Next, I will use my own bloody example to analyze some common stolen experiences for you to guard against theft! Don't ask me what feels like losing my cell phone. Thank you.

Internet cafes:

Someone will be attracted to your attention, and the other will take away your mobile phone. The entire process does not exceed five seconds. The Meizu M8 that I stole for the first time is such a situation! Keep in mind that mobile phones should not be placed on the table at the Internet cafes. Even if they are released, they must ensure that they do not leave their phones.
Subway entrance and so on:
Subway traffic is high, stealing mobile phones here can quickly transfer the target. My girlfriend is in the subway station, with the headset calling the phone was lost, there is no little defense. The next day she went to the unit and found out that she was not alone. There were three people in the same office with headphones stolen from the subway station. So in a similar place in the subway station, be sure to put your phone in your pocket or clutch it!
Storm phone:


This includes, but is not limited to, putting the phone in a loose pocket, a non-zippered backpack, the outermost pocket of a school bag, or places unattended when playing basketball in public. This is equivalent to saying to the thief, steal me and steal me! Well, that's it. My girlfriend had a mobile phone that was taken by a foreigner when she was internship abroad. Such a method took the phone, and it was after a long time that she was reminded that the schoolbag was not pulled.

For mobile phones, we really need to hold a twelfth of vigilance, on the one hand because of their hard-earned money lost pity, but also because those who can not be cheap thieves! The black industrial chain behind the mobile phone has its own business and public security to manage. What we need to do is to look at our mobile phone and not lose it! If it is really lost, then I will teach you how to let the thief take the initiative to send your phone back:
A buddy was stolen from a cell phone near the train station and immediately asked a friend to send a message to his cell phone: "Brother, the train is going fast. I can't wait for you, I got on the train! I owe you twenty thousand dollars. I In the locker room A19, the code is 1685â€. Half an hour later, the second cargo stolen from the phone was oystered in front of the A19 locker at the train station.